![]()
In the rapidly evolving landscape of the digital age, the significance of data privacy has reached unprecedented heights. As individuals, businesses, and governments harness the power of technology to streamline processes and enhance efficiency, concerns about the security and privacy of personal information have become more pronounced than ever. One technology that has emerged as a potential solution to these concerns is blockchain.
Understanding the Need for Data Privacy
The digital age has brought about a profound transformation in the way information is generated, processed, and shared. From social media interactions to financial transactions, a vast amount of personal data is constantly being produced and exchanged. This proliferation of data has led to a growing awareness of the need to protect individual privacy from unauthorized access and misuse.
In recent years, high-profile data breaches and incidents of personal information being exploited for nefarious purposes have underscored the urgency of addressing data privacy concerns. As a response to these challenges, blockchain technology has gained attention for its potential to revolutionize the way we manage and secure data.
The Promise of Blockchain Technology
Blockchain is a technology that operates on a decentralized and distributed ledger system, allowing for secure, transparent, and unalterable record-keeping. Unlike traditional centralized databases, where a single entity controls access and modifications, blockchain distributes control across a network of nodes. Each block in the chain contains a timestamped and encrypted record of transactions, creating an immutable and transparent history.
This decentralized nature of blockchain holds the promise of enhancing data privacy by reducing the risk of unauthorized access and manipulation. However, the implementation of blockchain technology alone is not a silver bullet for data privacy concerns. Striking the right balance between transparency and security is crucial for maximizing the potential benefits of blockchain while addressing its limitations.
Balancing Transparency and Security on the Blockchain
1. Transparent Yet Pseudonymous:
– Blockchain transactions are transparent and traceable, but they are often pseudonymous. While this ensures accountability, it also protects the identities of users. Striking the right balance involves maintaining transparency for accountability without compromising individual privacy.
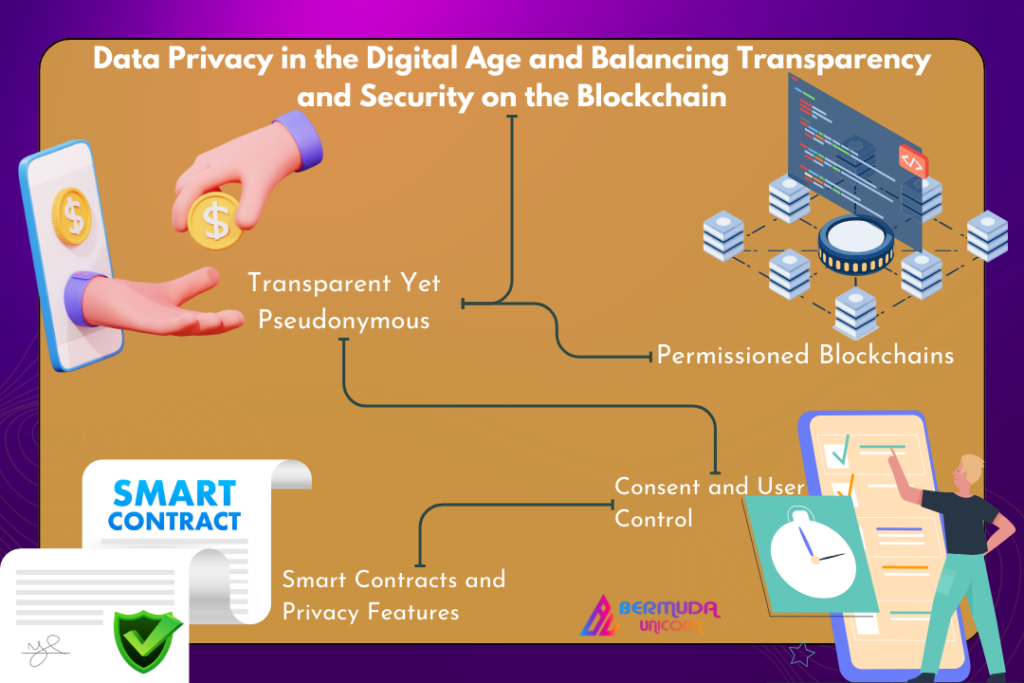
2. Permissioned Blockchains:
– Permissioned blockchains restrict access to authorized participants, offering a controlled environment. This approach is particularly relevant for enterprises and government applications, where sensitive information needs to be shared securely among known entities.
3. Smart Contracts and Privacy Features:
– Smart contracts, self-executing contracts with the terms directly written into code, can be designed with privacy features. This enables selective disclosure of information, ensuring that only relevant parties have access to specific details while maintaining the integrity of the overall transaction.
4. Consent and User Control:
– Incorporating user consent and control mechanisms within blockchain applications empowers individuals to manage their data. This can include granular control over who can access their information and for what purpose.
Challenges and Considerations
Despite the potential benefits, blockchain technology is not without its challenges in the realm of data privacy. Issues such as scalability, interoperability, and regulatory compliance must be addressed to unlock the full potential of blockchain in securing sensitive information. Additionally, the evolving legal and ethical landscape surrounding data privacy requires ongoing adaptation and collaboration between technology innovators, regulators, and the public.
Conclusion
As we navigate the digital age, the quest for a robust data privacy framework continues. Blockchain technology, with its decentralized and transparent nature, holds immense promise in reshaping the way we approach data security. By carefully balancing transparency and security, and incorporating privacy-centric features, blockchain can be a powerful tool in safeguarding personal information in our increasingly interconnected world. As the technology matures and stakeholders collaborate to address its challenges, the vision of a future where data is both secure and transparent may well be within reach.
FAQs
What is the role of blockchain in enhancing data privacy?
Blockchain serves as a decentralized and tamper-proof ledger, providing increased security and transparency for data transactions. Its cryptographic features and distributed nature make unauthorized access and manipulation more challenging, contributing to enhanced data privacy.
How does blockchain balance transparency and security?
Blockchain achieves a balance by maintaining transparent, traceable transactions while often using pseudonyms to protect user identities. Smart contracts and permissioned blockchains offer additional tools to control data access, ensuring that relevant parties have the necessary information while preserving overall transaction integrity.
Can blockchain ensure complete anonymity in transactions?
While blockchain transactions are pseudonymous, achieving complete anonymity can be challenging. Users’ identities may still be inferred through various means. Blockchain focuses on providing a level of privacy through pseudonymity while emphasizing transparency and accountability.
What are the challenges associated with implementing blockchain for data privacy?
Challenges include scalability issues, interoperability concerns with existing systems, and the need for compliance with evolving regulations. Addressing these challenges is essential for the widespread adoption of blockchain in data-sensitive applications.
How can individuals control their data on a blockchain?
Blockchain applications can incorporate features that empower individuals, such as consent mechanisms and user-controlled access. Through these tools, individuals can manage who has access to their data, for what purposes, and maintain a level of control over the use of their personal information.
